CyberShield
Cybersecurity Training Platform
All-in-one platform consolidates pen-testing, training, monitoring, and analytics—replacing 4+ separate tools for comprehensive school protection.
All-in-One Platform Replaces 4+ Tools.
Built Specifically for Education.
Comprehensive Security Without the Complexity
CyberShield consolidates pen-testing, training, monitoring, and analytics into one education-focused platform designed specifically for K-12 and universities.
All-in-One Platform
Pen-testing, training, monitoring, and analytics in one unified platform—no more juggling separate tools and vendor contracts.
Education-Specific
Built for school vulnerabilities and compliance requirements, not generic enterprise—including unique VIP face protection for school leaders.
AI-Powered Protection
Cyber Fortune AI predicts emerging threats before they strike, while automated pen-testing continuously scans for vulnerabilities.
Core Features
What Makes CyberShield Different
From AI-powered threat prediction to education-specific remediation guides, CyberShield delivers comprehensive security capabilities designed specifically for K-12 schools, universities, and school districts.
33 Interactive Scenarios
Hands-on training modules designed for students, staff, and IT personnel—from phishing awareness to incident response.
24/7 Web Monitoring
Real-time content monitoring with instant alerts for threats, including VIP face protection for school leaders.
Automated Pen-Testing
Continuous vulnerability scanning identifies weaknesses before attackers do—no security expertise required.
Cyber Fortune AI
AI-powered threat prediction analyzes patterns to anticipate and prevent emerging attacks.
61+ Remediation Guides
Step-by-step instructions tailored for educational institutions—from basic fixes to advanced security measures.
Comprehensive Analytics
Track security posture, training completion, threat trends, and compliance status in one dashboard.
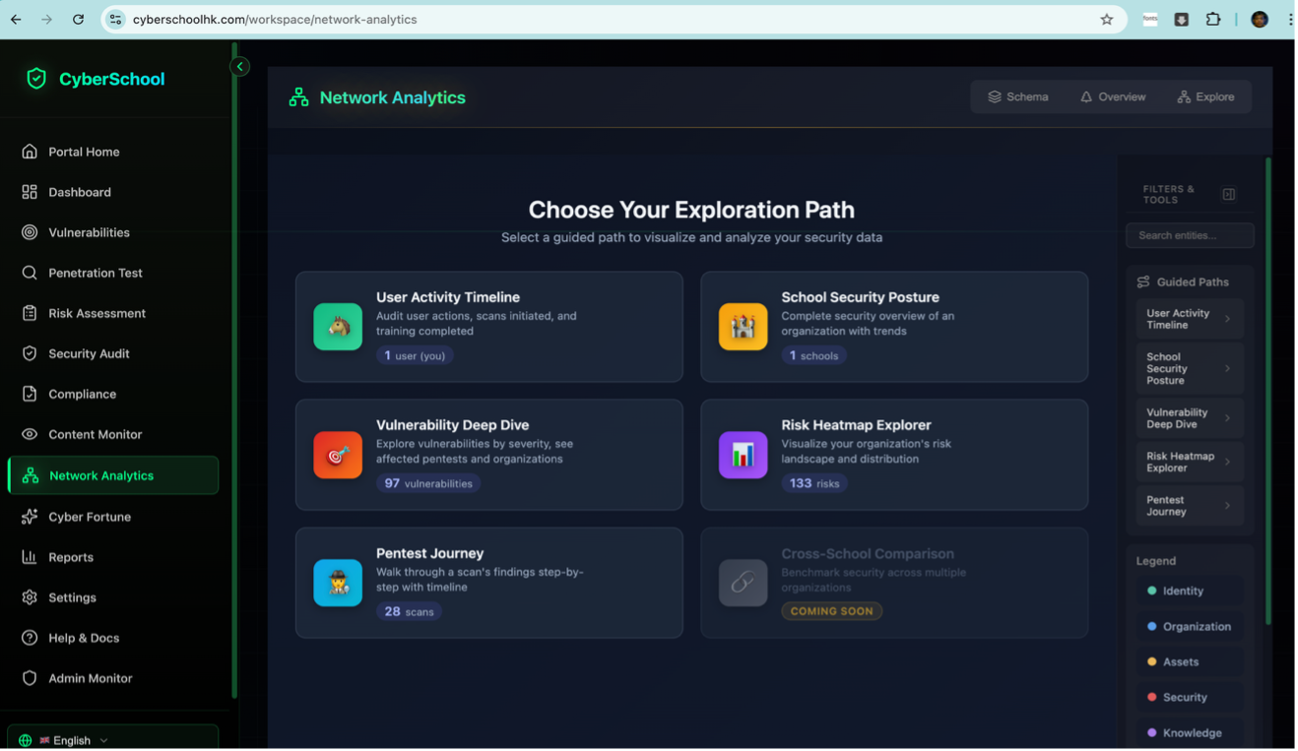
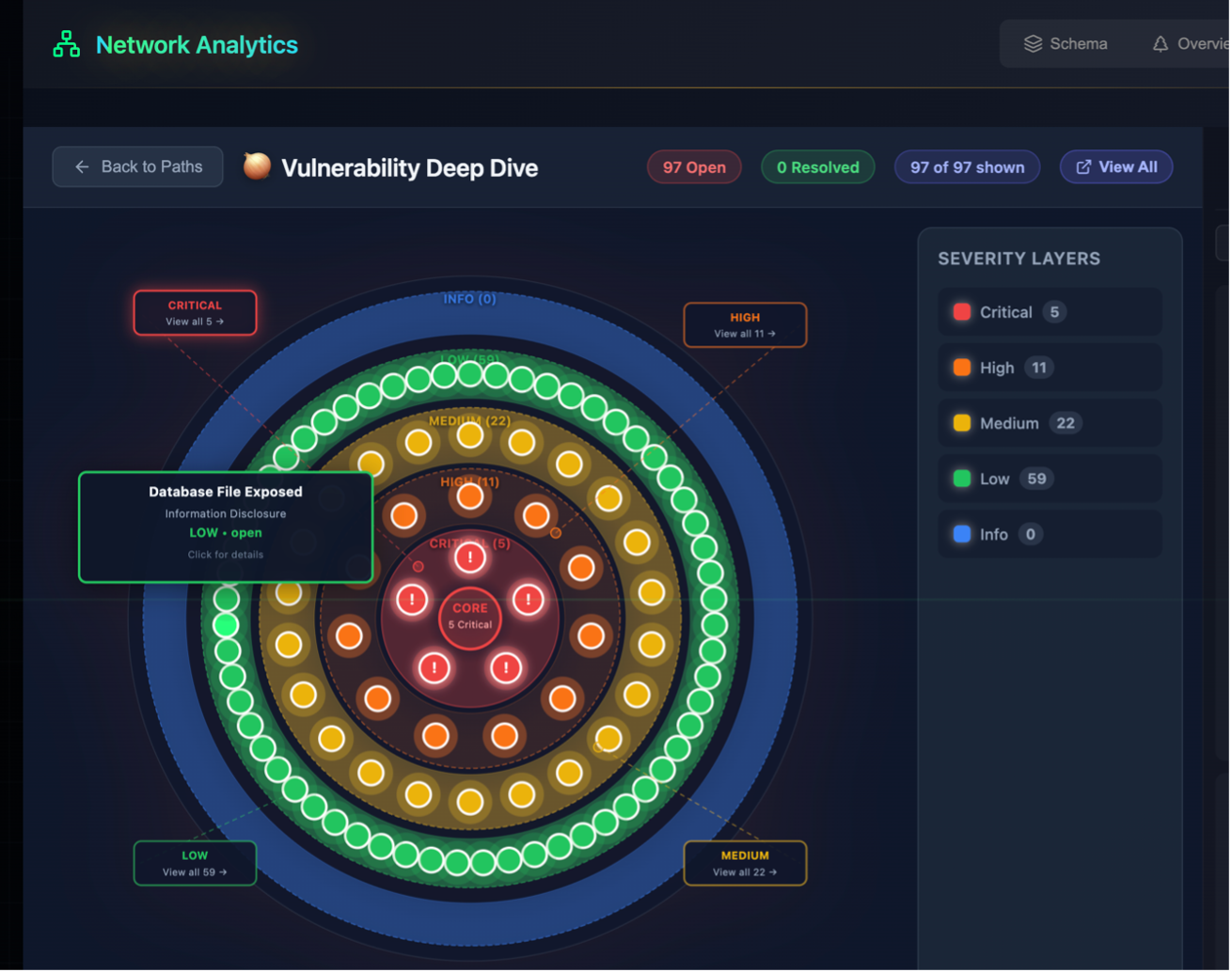
Platform Overview
See CyberShield in Action
Intuitive dashboards for security monitoring, interactive training scenarios, and comprehensive threat analytics—all designed for educational environments.
Choose Your Protection Level
Flexible tiers designed to match your school's size and security requirements.
Silver
Essential security for small schools
- ✓Core security features
- ✓Basic training scenarios
- ✓Automated monitoring
- ✓Standard reports
Gold
Advanced security with insurance
- ✓All Silver features
- ✓33 training scenarios
- ✓Cyber liability insurance
- ✓Advanced analytics
- ✓Priority support
Platinum
Enterprise-grade protection
- ✓All Gold features
- ✓Unlimited domains
- ✓24/7 dedicated consultant
- ✓Custom training modules
- ✓White-label options
Download Solution Brief
Get our comprehensive guide on protecting your school with CyberShield.
Ready to Transform Your Data?
Try GQLDB Playground or contact us for enterprise solutions.